As a Managed Services Provider (“MSP”), security is at the forefront of our focus. In a recent Insight, “Email Security: The More Things Change, The More They Stay the Same”, we highlighted several key concepts:
- Email continues to be the leading attack vector for all types of security breaches.
- Email security providers saw a 64% rise in email-based threats within the past year.
- Good security strategy involves a layered approach, with Email Security and Backup as critical components.
Many organizations using Microsoft 365 (or Office 365) for email believe that they have sufficiently addressed their email security and backup needs. However, only 6% of Microsoft customers are purchasing SKUs that include advanced security features. Compounding the risk, according to Business Wire, 97% of users are still unable to detect a sophisticated phishing attack. Additionally, SaaS vendors, such as Microsoft, suggest their customers use alternative backup solutions when planning for and combatting everyday cyber attacks.
The good news is that if your organization has the basic Microsoft security capabilities—such as Microsoft Exchange online protection and Windows Defender for Microsoft 365—that’s a step in the right direction. The bad news is that Microsoft is the #1 target, and bad actors design attacks to defeat their detection.
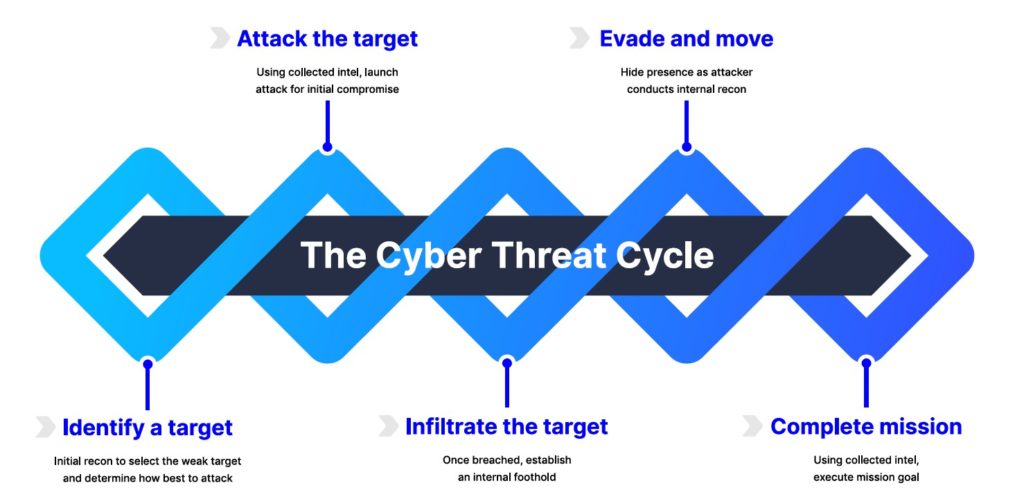
The Cyber Threat Cycle
The Cyber Threat Cycle describes five major activities bad actors perform.
- Identify a target – By sending a seemingly innocent email, threat actors can collect a lot of information, from the type of security gateway in place to whether the user actually exists and is willing to engage.
- Attack the target – From an analysis of hundreds of thousands of breaches over recent years, email has been the easiest way to gain initial entry to an endpoint or internal server in the majority of instances.
- Infiltrate the target – Gaining access to a single system does not automatically result in a completed mission. Threat actors will often attempt to establish a foothold by increasing or elevating the credentials they have obtained.
- Evade and move – Compromising a user’s inbox is a common technique for gaining more information about an organization’s business processes and personnel. Yet, threat actors are cunning enough to augment mailbox rules to avoid detection, sometimes for years.
- Complete the mission – At this point, it is a matter of mitigating or containing the execution of the mission goal—whether exfiltrating sensitive data, forcing a wire transfer, or wreaking havoc by corrupting critical data—before the breach makes headlines.
Once you understand the Cyber Threat Cycle, you can begin to implement a proactive security strategy that will close 95% of your attack prevention gap.
When an attack occurs, the deeper you find yourself within the Cyber Threat Cycle, the more business interruption will occur. So, a tactical and layered security strategy is imperative. Implementing preventative steps such as email threat detection and email encryption substantially mitigate the risk of initial compromise.
Your Email Resilience Strategy
Your strategy to address email vulnerability does not have to be hard work or complex, and we, along with our security partners, recommend a three-pronged approach to achieve Email Resilience:
- Protect: Prevent cloud vulnerabilities
- Detect: Identify and alert to the presence of threats
- Respond: Contain and remediate threats

1. Protect: Prevent cloud vulnerabilities
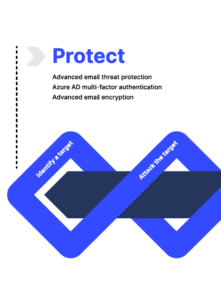
- Email is a treasure trove of reconnaissance information for bad actors.
- Email attacks are cheap for hackers to execute.
- Employees are no more effective at detecting a phishing attack intended to steal their credentials or malware aimed to compromise their devices than they were years ago.
Even if you have security tools like Microsoft Exchange online protection and Windows Defender for Microsoft 365, a multi-layered email defense is required to defend your most vulnerable point of entry further. You can substantially mitigate the risk of initial compromise with an advanced threat protection and email encryption solution, along with enforcing multi-factor authentication for user logins.
2. Detect: Identify and alert to the presence of threats
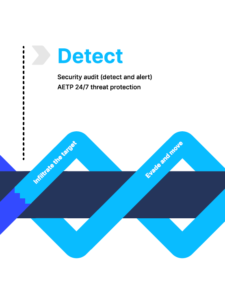
Incorporating a security audit and monitoring process that focuses on the following can help close this gap:
- Identifying weaknesses in user login and authentication
- Identifying suspicious behavior related to mailbox rules and email communication
3. Respond: Contain and remediate threats
- Remove any malicious email that may have been delivered to an employee’s inbox.
- Scan the targeted employee’s login activity and require vulnerable passwords to be changed (and enforce MFA if disabled).
- Clear an employee’s file systems and provide a clean backup of their data.
Our email backup and recovery services, along with the rest of our security suite, allow your employees to remain productive—even during an attack.
Taking Action
Along with our security partner, Zix | AppRiver, implementing this simple, three-pronged security strategy will help address what are potentially significant gaps in the #1 security risk to your company—email—and enable you to become more resilient!
As an added benefit, when you partner with Abel Solutions for your productivity and security needs, you get access to our robust email auditing platform at no charge. See it for yourself by scheduling a complimentary security audit today!
This Abel Insight was written by Abel Solutions’ President, David Hammond.
As a Microsoft Gold Partner and a Zix | AppRiver Platinum Partner, we are ready to walk you through implementing your straightforward security strategy.