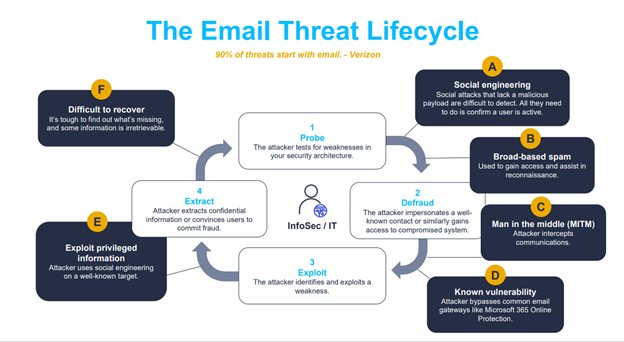
Security threats are a dime a dozen. Every week we learn about a new flaw or exploit that could put our businesses and data at risk. Whether it’s ransomware shutting down operations or data breaches exposing sensitive financial information and personal data, security incidents have become so common that they’re no longer surprising.
What might come as a surprise is that email remains the leading attack vector for all types of malicious activity1. Just as a sales professional can reach hundreds of potential leads with a single message, malicious actors can distribute their content with the same ease. They can target thousands of addresses while sipping their morning coffee, and it doesn’t take much for them to see a quick return on their investment. In this Insight, we’re going to look at the current state of email security, some of the strategies leveraged by malicious actors, and evolving methods available to protect against them.
Email Security Today
With employees worldwide trading their conference rooms and cubes for home offices, virtual meetings, and document collaboration, cybercriminals saw new opportunities to bypass company defenses. Email security providers saw a 64% rise in email-based threats, and end-users were three times more likely to click a malicious link in an email.
In addition to the increased volume, we saw a significant increase in the sophistication of their attempts. Gone are the days of the obvious malicious email, full of spelling mistakes and poor grammar. Malicious actors were quick to take advantage of the latest news headlines, and Covid-19 themed malware and phishing lures dominated. It was clear that they saw the value in crafting higher-quality content.
We also saw a significant rise in business email compromise (BEC) attacks in the form of impersonation fraud, with an almost 53% increase over the previous year. Cybercriminals are increasingly leveraging social media to identify their next targets and gain insights into the company and its people. Two things remain clear, email is still the leading attack vector used by cybercriminals, and the end-user is more vulnerable than ever.
Email Security Defined
A good security strategy involves a layered approach, and one of the key layers is Email Security. This typically takes the form of a 3rd party service or appliance that processes inbound emails to confirm they are safe and legitimate before passing them on to the end-user. Many services and products on the market cover this basic concept, but they are not all created equal. There are various features underneath the umbrella of Email Security that separate the leaders from everyone else.
AI-based scanning
Much like traditional Anti-virus products, email threat detection is moving away from pattern-based detection, which requires that the threat be known before it can be detected and blocked, to AI-based scanning that can analyze behavior patterns and other data to decide on the safety of the content.
Impersonation Detection
With the rise in BEC impersonation fraud and the ease with which criminals can obtain detailed information about the stakeholders within a company, email security products need to be able to identify impersonation attempts. Many BEC scams take the form of an email sent from an outside address but with the name of a business stakeholder on it. Since most people focus on the sender’s name and not the email address, it’s easy to trick someone this way. Modern impersonation detection systems can detect these attempts and flag them as potentially fraudulent.
Attachment sandboxing
Rather than simply scanning an attachment for known malware, attachment sandboxing will first open the attachment in a secure location, separate from the user and their system, to analyze the file and its behaviors before passing it on to the end-user.
Link protection
Link protection systems function similarly to attachment sandboxing, where the link in the email is replaced with a secure version that points to the service provider’s secure location. This allows for the host location of the link to be analyzed and acted upon before the end-user clicks it.
The human factor
The human factor is still the biggest potential flaw in any security plan. With the prevalence of work-from-anywhere and the combination of comfort and distractions it presents, it’s easier than ever for employees to fall into a routine that results in something being opened, clicked, or responded to inadvertently. When combined with the possibility that malicious actors may actively target your business, the risk only increases.
It’s not uncommon for businesses to think that technology is the solution to this problem and that because their employees are not in technical roles, they cannot understand those things, but that couldn’t be further from the truth. Through education and consistent reinforcement of basic security concepts, you can build a network of awareness that is far more effective than any technical solution.
Many threat simulation and security awareness training services allow you to send regular simulated threat emails to your users. Typically, these emails are designed to mimic the types of threats used by cybercriminals. Most can be customized to be as tricky as needed or target specific areas that may impact your business. This serves to increase the overall awareness of your userbase and give you clear metrics on your employees and their susceptibility to these types of threats. Most of these services include awareness training. If an employee fails a simulation test, they will be automatically enrolled in training relevant to the type of simulation sent. You can also schedule regular training for all users to continue to cultivate a security-forward mindset.
Be prepared
Businesses rely more than ever on digital communication, especially email, yet many companies don’t have an adequate plan and the necessary tools to safeguard this door into their organization.
This Insight highlights the continued risk presented by email-based threats and reviews some of the technical and human-facing methods that can be used to protect your business from those threats.
Whether you need assistance in planning, deploying, and managing an email security system or would like a managed security awareness service for your business, Abel Solutions is here to help. Contact us today to get started!
1 2021-email-threat-report.pdf (azureedge.net)
This Abel Insight was written by Abel Solutions’ IT Services Manager, Jason Casteel.