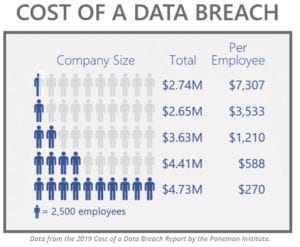
Among the top concerns of cloud implementations is the security and loss of data. We have all heard the news reports of large corporations who are the victim of a cybercrime. According to a 2019 study from the Ponemon Institute, the cost of a data breach is close to 4 million dollars. The loss of data has far-reaching implications from lost business to regulatory fines and remediation costs not to mention the fallout with customers and business partners.
Identifying and preventing those inside your organization from either inadvertently or intentionally sending confidential information outside your organization is made more attainable with the advancements of machine learning and artificial intelligence. The built-in Office 365 security features and tools to ensure your data is secure.
A common misconception regarding the Office 365 security and compliance features are that they good-to-go without intervention from the business owner or IT personnel. The truth is Microsoft offers many tools and suggestions for keeping your data safe. Still, they all require time, effort, and security knowledge to configure correctly.
There are two new features recently available that are of importance: Information Protection with Sensitivity Labels and Insider Risk Management.
Data Classification and Sensitivity Labels
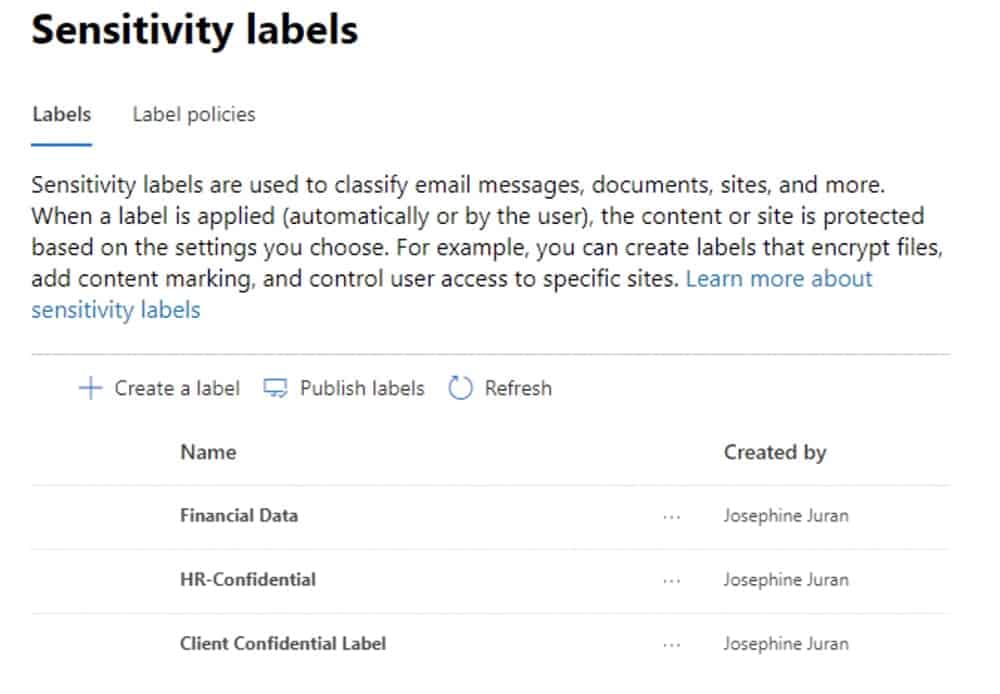
Classifying content across Office 365 services entails the use of Office 365 labels. These labels are used for records management and follow governance rules as laid out by the organization and by legal authorities.
Sensitivity labels allow sensitive content to be labeled and protected without hindering productivity and collaboration between users. They can be used to:
• Enforce protection settings, including encryption and watermarks, on labeled content;
• Protect Office app content across platforms and devices;
• Prevent sensitive data from leaving your organization on devices running Windows;
• Protect content in third-party apps and services;
• Extend sensitivity labels to apps and services of third-parties; and
• Classify content without using protection settings.
How does a sensitivity label work?
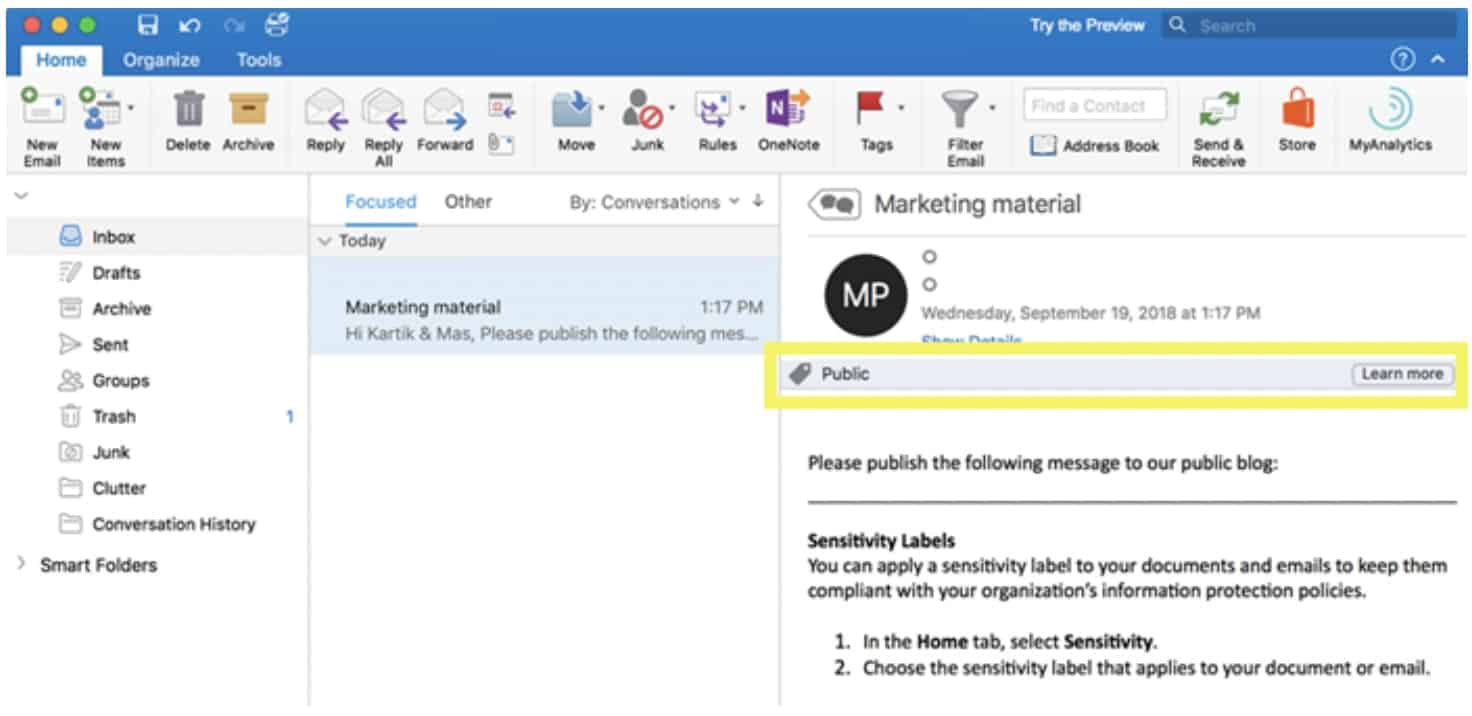
Sensitivity labels classify data across the organization and enforce protection settings based on that classification. In the Office 365 apps, labels operate like tags in the sense that they are customizable, persistent and presented in clear text.
Different levels of sensitive content can be defined as categories. These include Public, Personal, General, Confidential and Highly Confidential. Third-party apps and services can read the clear text, allowing them to apply protective actions as dictated. Once applied, the sensitivity labels persist in the metadata of the document or email. This means that the label travels with the content. The label becomes the basis for applying and enforcing policies as it includes the protection settings.
Protection settings for sensitive labels include:
• Encryption on email and/or documents whereby specific users or groups can be granted permissions to perform actions and for how long;
• Marking content through the use of watermarks, headers, or footers to documents or emails;
• Prevent data loss with endpoint protection which works with all Windows devices; and
• Automatically apply labels to sensitive data content as opposed to manually applying labels. With manual application, users are prompted to apply the recommended label, whereas with auto-apply, the criteria will determine the label that is automatically applied.
Insider Risk Management
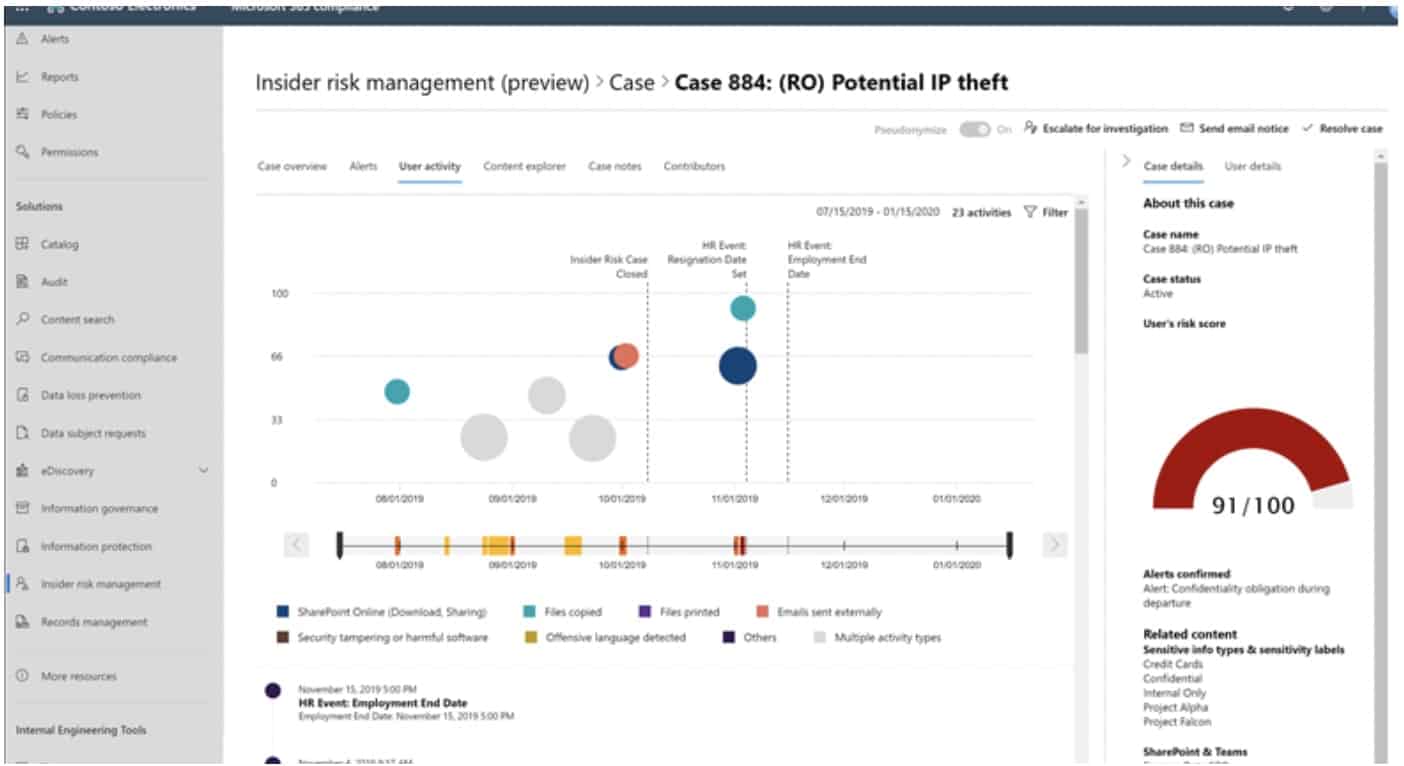
Insider Risk Management provides the ability to detect, investigate, and act on risky activities the occur within Office 365. When you establish policies, this allows the detection of malicious and inadvertent risk activities that are transpiring within Office 365. Once detected, the ability to escalate a case directly to eDiscovery is available. Responsible individuals within your organization can then take the appropriate actions to ensure users are compliant with organizational compliance standards.
Managing the risk of a cloud-based service like Office 365 where users have access to create, manage, and share data, begins with understanding the types of risks. These risks include activities by employees that are illegal, inappropriate, unauthorized or unethical. These risks are manifested as:
• Leaks of sensitive data and data spillage;
• Confidentiality violations;
• Intellectual property (IP) theft;
• Fraud;
• Insider trading; and
• Regulatory compliance violations.
Insider Risk Management takes advantage of services and indicators to identify, triage and act on risk activity based on policies.
Through the use Office 365 logs and Microsoft Graph, Insider Risk Management allows you to define specific policies to identify risk indicators. These policies enable you to identify risky activities and to take action to mitigate these risks.
Insider Risk Management is centered around the following principles:
• Transparency: Balance employee privacy versus organization risk with privacy-by-design architecture.
• Configurable: Configure policies based on industry and business groups.
• Integrated: Integrate interactivity across Office 365 compliance solutions.
• Actionable: Provide insights to enable employee notifications, data investigations and employee investigations.
Minimize Your Risk and Maximize Your Investment
The ability to leverage the rapidly expanding capabilities of machine learning opens the possibilities to better recognize risky activities and to act quickly. Don’t fall victim to data loss or a breach. Engage with us to help your organization make the best use of the tools and features of Office 365 to ensure that you are maximizing your cloud investment and minimizing your risks.
This Abel Insight was written by Abel Solutions’ Farha Akhter, Sr. Developer, and Jason Bell, Chief Technologist.