Nonprofits in our communities exist to provide critical (dare I say “essential”) services to our most vulnerable neighbors. With over 1.5 million registered organizations in the United States alone, these nonprofits fill the need gap between what governments, corporations, foundations, and private citizens fund and the actual support beneficiaries (people, animals, and the environment) need.
However, as anyone knows who has donated to or volunteered with a nonprofit, spending money on technology is not typically at the top of their priority list. As a founding member and 15-year Board of Directors member of a nonprofit organization called The Drake House, resources are first and foremost allocated to the mission, which in The Drake House’s case is to provide housing (crisis and transitional) and education programs for homeless single mothers and their children in north metro Atlanta.
But what if the mission of a nonprofit was compromised by an information security breach? What if the private information about its beneficiaries was suddenly compromised? What if the valuable and limited resources of a nonprofit had to be spent recovering from a lapse in information security?
The State of Nonprofit Security and Data Privacy
Microsoft research indicates that it takes on average 80 days (or 11 weeks) to recover after the detection of a security intrusion. Whether you are a for-profit or a nonprofit organization, that length of time, and depending upon the severity of the security intrusion, the damage done to the organization’s reputation may not be recoverable.
Microsoft conducted a survey of fifty nonprofits through its partners TechSoup and NTen. Although most of the respondents indicated that their organization had a “modern” IT infrastructure, the survey determined that most did not use important cybersecurity controls.1 For example:
-
- 60% indicated that they did not have or know of their organization’s digital policies related to cybersecurity risk, equipment usage, and data privacy.
- 74% responded that they did not use multifactor authentication (MFA) to access organization assets and data.
- 46% reported that they use wireless printers, webcams, and other Bluetooth and wireless devices that are unsecured.
So, what can nonprofits do? There is not a nonprofit-specific standard for cybersecurity. Nonprofits can benefit, however, from the well-established, risk-based approaches to cybersecurity management that for-profit businesses use.
Cybersecurity Framework
Nonprofits can achieve greater resilience from cybersecurity threats by leveraging the U.S. National Institute of Standards and Technology (NIST) Cybersecurity Framework. As with frameworks, it is not a one-size-fits-all model but is intended to allow organizations to create a plan for and better manage cybersecurity risks in a cost-effective way. Per the framework, organizations should focus on six goals:
-
- Identify cybersecurity risks.
- Protect against threats.
- Detent cybersecurity incidents.
- Respond to incidents.
- Recover from incidents.
- Implement specific, high-value controls.
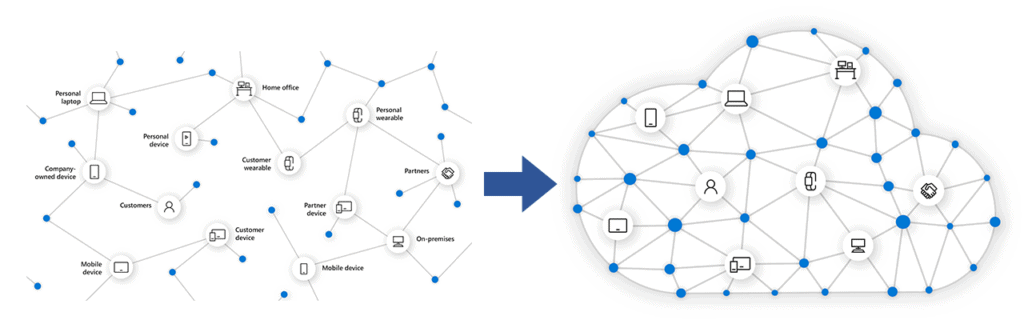
If this sounds like a big challenge for any organization, much less a nonprofit, it is. Fortunately, there is a path forward. The future of cybersecurity is in the cloud, and Microsoft’s trusted, public cloud is uniquely suited for this challenge due to its simplicity, speed, and scale.
Cybersecurity in the Cloud with Microsoft
IT teams and IT professionals find themselves increasingly responsible for providing security for a myriad of technologies and devices, most of which their organization does not own—i.e., employee-owned devices to access corporate data as well as other systems and devices owned by donors, beneficiaries and volunteers. Add to this all of the internet-connected devices such as printers, copiers, thermostats, refrigerators, etc., and an organization has vulnerabilities everywhere.
Microsoft’s cloud security technology investments cover four broad categories.
Identity and access management
The majority of security breaches begin with the single weakest link—compromised passwords. Therefore, the core of any security strategy is strong capabilities around secure authentication, conditional access, and identity protection. This includes risk-based conditional access, Multi-Factor Authentication, and the capability to identify high-risk usage of cloud apps and user behavior.
Threat protection
The sophistication and impact of attacks are ever-increasing, so organizations need automated threat protection that is always evolving. This includes Advanced Threat Protection for Office 365, Azure, and Windows as well as cloud app security for your SaaS applications.
Information protection
Sixty-four percent of organizations report that employees share PII and other sensitive business data externally without it being encrypted.2 Therefore, protection of your information, wherever it travels, is a priority. Capabilities include the ability to discover and classify sensitive information (Intelligent Classification and Tagging of content) and apply protection to information based on policies (Data Loss Prevention).
Cloud security
As more organizations move more to the cloud, they need comprehensive cloud security regardless of which cloud or cloud-based applications they use—from Azure to AWS and from Slack to Salesforce.
Summary
Nonprofits often lack the budget, technology expertise, and staff time necessary to plan and implement sophisticated security and data privacy protection; however, they are no less susceptible to breaches and in many cases are far less prepared to recover from them. With a shift to cloud technologies, nonprofits can benefit from the built-in capabilities that are available that otherwise would be out-of-reach for legacy on-premises systems.
Engage with us to assess your current security state to help you understand how secure your organization really is and to create a security roadmap to help you reach your security objectives.
This month’s Abel Insight was written by Abel Solutions’ President, David Hammond.
1. Microsoft Guidelines for Cybersecurity and Privacy report.
2. Egress + OpinionMatters survey: https://www.businesswire.com/news/home/20190221005061/en/Survey-83-Percent-U.S.-Organizations-Accidentally-Exposed